Originally published ItSecurityGuru @ https://www.itsecurityguru.org/2015/05/27/the-great-cyber-comparison-anthropology-of-modern-malware-and-development-of-civilizations/
In his Pulitzer Prize-winning Guns, Germs and Steel, Jared Diamond investigates 13,000 years of human society and how it unfolded differently across the continents. He poses questions such as, “Why didn’t capitalism flourish in native Mexico, mercantilism in sub-Sahara Africa, scientific inquiry in China, advanced technology in Native North America, and nasty germs in aboriginal Australia?” Mr. Diamond concludes that the key differences in how society evolved was due to continental environments and not human biology.
Features of a complex society, such as advanced technology and centralized political organization emerged only in dense, sedentary populations that were capable of accumulating food surpluses. Those wild animal species suitable for domestication were consolidated in just nine small areas of the globe, so it made sense that the earliest signs of the rise of agriculture appeared in these areas. And all of them were in close proximity to those dense and lazy populations.The modern technology of the day, guns, horses, and diseases enabled the more evolved societies to conquer the lesser-developed and more spread out populations. Cybersecurity has similar points in its history where leaps in technology and service adoption created opportunities that triggered evolutionary events in cyber attacks. Two disparate evolutions, civilization and cybersecurity are similar upon closer questioning: “Why does malware tend to originate from only a few geographical areas? How did mass adoption of the Internet and online services impact cybersecurity? And what drove the already destructive virus industry to evolve into targeted malware that can bypass many of today’s defenses as they zero in on their victim?
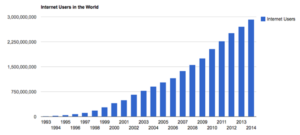
In 1988, when the Morris worm was written, it was estimated that there were sixty thousand computers connected to the Internet. With its small attack surface (number of potential targets) the damage caused by the Morris worm was tiny compared to our current risk. According to Cisco somewhere between eight to ten billion devices are connected to the Internet today. Our current potential attack surface has grown from the population of a mid-size suburb to more than the entire population of this planet!! In 1995 only one percent of the world’s population had an Internet connection—now that number is close to 40 percent. The coming growth from the explosion of the Internet of Things will grow this exponentially more: Gartner is forecasting twenty-five billion connected devices by 2020!
Source: Internetlivestats.com
So, what has all this growth caused? A new generation of devices with unknown vulnerabilities; an increase in the number of users with Internet connected devices who do not know their machines are at risk; an increasing exposure gap between when a vulnerability is known and when a significant number of users have patched it; a growing attack surface that offers attackers a smorgasbord of low hanging fruit. Ultimately it just may have to be the weight of our own innovation that forces us to sit up and take cybersecurity seriously. The Internet of Things is growing at an alarming (depending upon your perspective) rate. Don’t misunderstand me, innovation is the root of my life and I love my gadgets that help fund Kickstarter projects. But irony is co-pilot to these “Things” that make our lives easier—all it takes is a piece of code to be delivered to one of these products, and suddenly our lives have become much more difficult.
Cyber attackers are a fast-moving, adaptable bunch, and so are their tools. Attacks have changed in a multitude of ways to take advantage of the growing attack surface, but so have the technologies in place to prevent them. When we stop to consider how far the digital age has driven technology and its adoption, it shouldn’t be a surprise that the technology behind those pesky viruses from the late 80s have evolved into behemoths that are capable of taking down multinational corporations or even governments. The surprise will be whether we are capable of stopping them. More on how attacks have evolved in upcoming segments.
No comments:
Post a Comment